SCA stepped out from behind SAST/DAST long shadow to prove its worth years ago. And, thanks to ambitious bad actors, the complex software supply chain, and genAI coding assistants accelerating overall code volume, SCA solutions are essential to clean up the supply chain and bolster application security.
SCA is also an app sec darling for its ability to generate software bill of materials (SBOMs). With the EU CRA Act finalized, the proposed U.S. DOD Software Fast Track (SWFT) initiative requiring SBOMs, and governments such as Australia Australian government guidelines for software development that includes SBOMs, more software suppliers around the world will need to provide SBOMs to win and maintain business. Advanced SCA tools go beyond just generating an SBOM, they continuously monitor it for newly disclosed vulnerabilities to proactively alert and will ingest 3rd party SBOMs to identify the risk of incorporating a third-party component.
Opportunistic attacks that take advantage of newly introduced vulnerabilities and unpatched software require patience and timing. But attackers can be proactive by directly poisoning open source and third-party components. These types of attacks such as dependency confusion and typo squatting were already on the rise. But now, “slopsquatting” happens when AI hallucinates package names developers must add. Additionally, bad actors willing to play the long game, typically affiliated with nation states, will bully their way into maintaining obscure but widely used open-source software dependencies such as xz utils to bury malicious code and target downstream recipients. SCA solutions provide insight into open-source component health during selection and actively block malicious packages from being downloaded. Clearly SCA is the app sec hero we need.
Enterprises have been eager to embed and utilize AI in the customer-facing applications that they build. In Forrester’s 2024 survey of business and technology professionals, 33% reported using genAI in production applications. This means a whole new world of application dependencies comprised of AI models, third-party APIs, and open source dependencies. Python is a popular language for AI applications as is the pypi package manager for open-source dependencies. Bad actors did not waste any time in uploading legitimate looking but malicious packages that were downloaded hundreds of times by developers building AI applications. Poisoned AI models could be pulled down from hugging face and other public repositories. At the time of The Forrester Wave: Software Composition Analysis Software, Q4 2024 evaluation, only a few SCA vendors were scanning AI models or creating AI-boms, but this functionality is needed broadly and quickly.
When thinking about purchasing or upgrading your SCA software, consider key insights we gathered from talking with SCA vendor customer references to get not only the tool you deserve but also need.
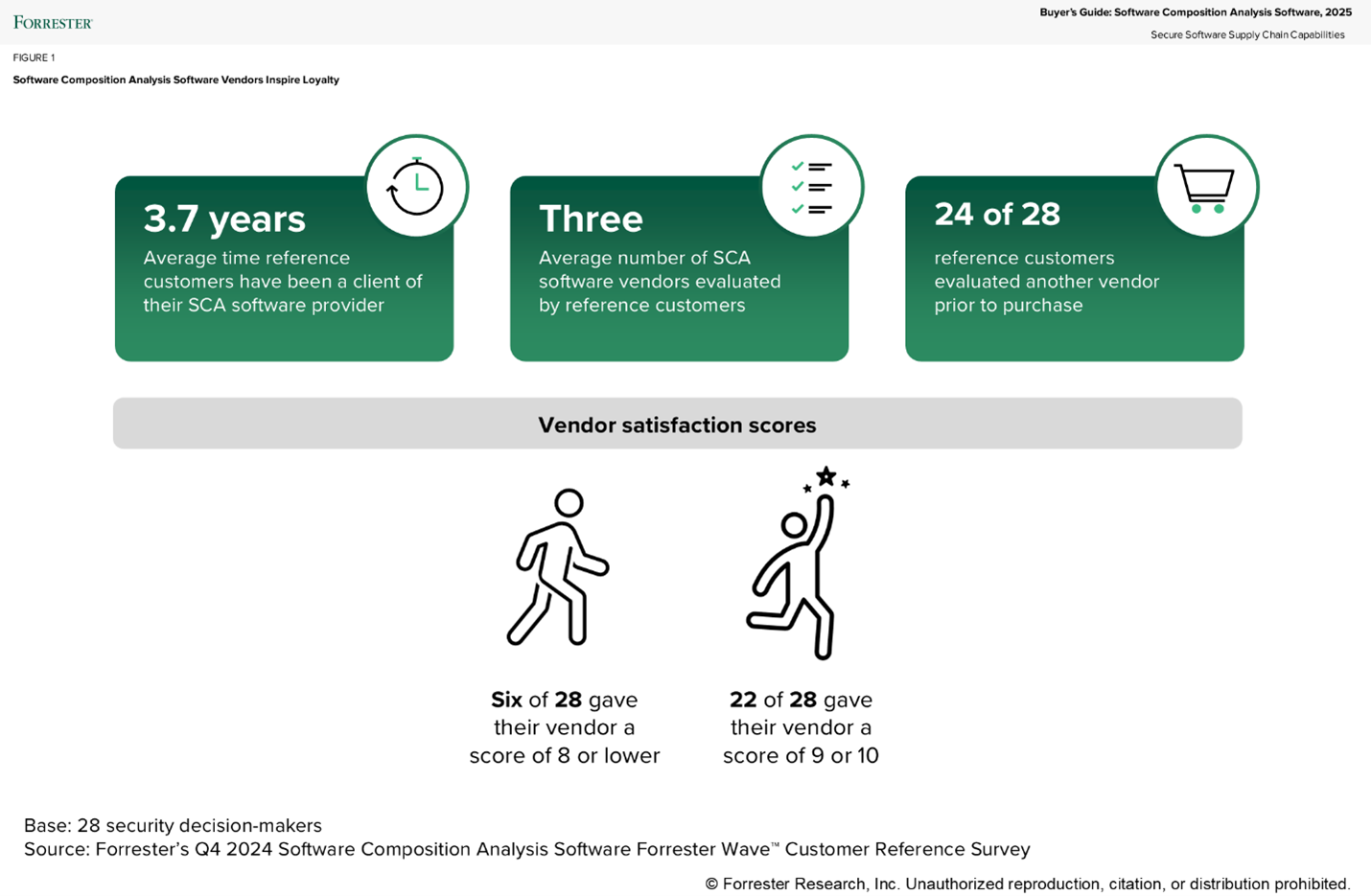
- Evaluate more than one vendor. This may seem obvious, but SCA software differs in functionality and the quality of output. Some software is primarily focused on open-source components while others go beyond and assess third-party components and even inner source components (those shared components written by your organization). The quality of the results also differs based on language and ability to detect vulnerabilities in transitive dependencies. Most reference customers evaluated three vendor software as part of the purchasing process (see figure below).
- Don’t settle. You are going to be in it for the long haul. Customer references have been with the vendor on average for over 3.5 years. And they are happy! Twenty-two of 28 references rate their vendor at 9 or 10. If you have an SCA solution and you are not satisfied, it is worth your time to revisit at the next renewal period.
- Keep an eye out for the extras. SCA software vendors have expanded their offering to cover more of the software supply chain such as offering malicious package detection and package firewall protection, IAC and container image scanning, and secrets detection. Depending on the vendor and their pricing and packaging model, these capabilities could be add-ons to the base price. Static reachability (the ability to determine if the vulnerable function is called by the first-party code) should be table stakes for SCA solutions but some vendors require you purchase their static application security testing (SAST) solution in addition to get this level of insight.
Be your company’s hero and select a SCA software solution that helps secure your software supply chain by utilizing Forrester’s Buyer’s Guide: Software Composition Analysis Software, 2025 and The Forrester Wave™: Software Composition Analysis Software, Q4 2024. For more insights, schedule a guidance session or inquiry with me. Protecting your brand, your customers data, and your revenue is worth the effort.







